
In the world of WEB3, security always been the most concerned by everyone. How to better protect our own assets, in addition to choosing safe tools, what is more important is our own security awareness and usage habits.
On-chain transfer operations cannot be rolled back. If someone tells you that you can get it back for a fee, it must be a liar.
Assets are stolen, generally for two reasons. Either the private key was leaked, or the address was malicious approval.
About malicious approval, here is a case: Malicious approval disguised as a transfer page
Judy has been in touch with crypto for a while, and has also met some friends. One day, a friend of hers contacted her and said he wanted to buy her USDT Token, which was higher than the market price. This friend also asked to make a small transaction first, and pay Judy first, to gain Judy’s trust. Then provide Judy with a QR code and guide her to scan the QR code to transfer .
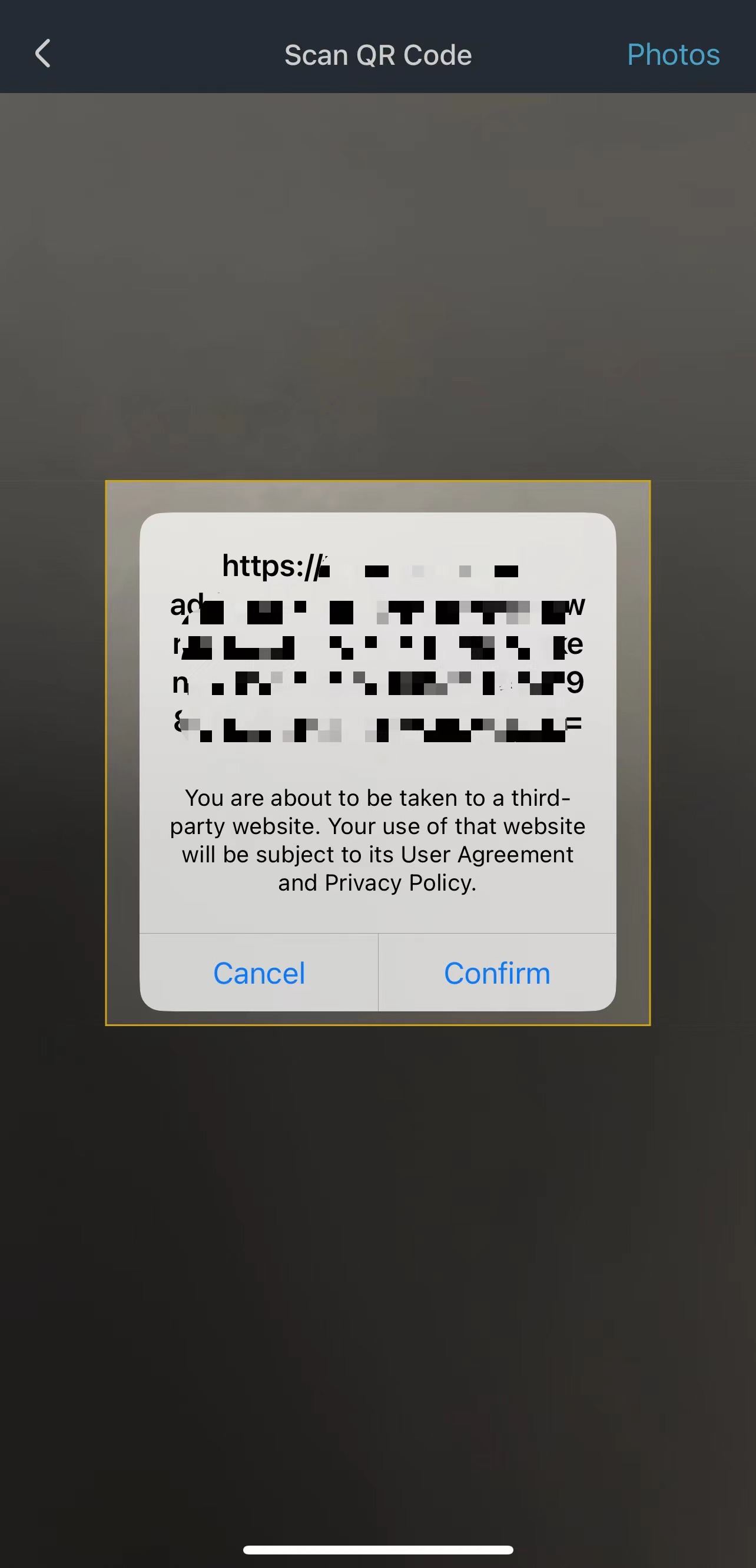
The QR code jumps to a URL, which is carefully crafted by the scammer to look like a transfer page. As long as Judy performs the signature operation, it will be maliciously approval. Since it was a small amount and the payment was received, Judy didn’t think much about it, and followed the scammer’s guidance to complete the first transaction.
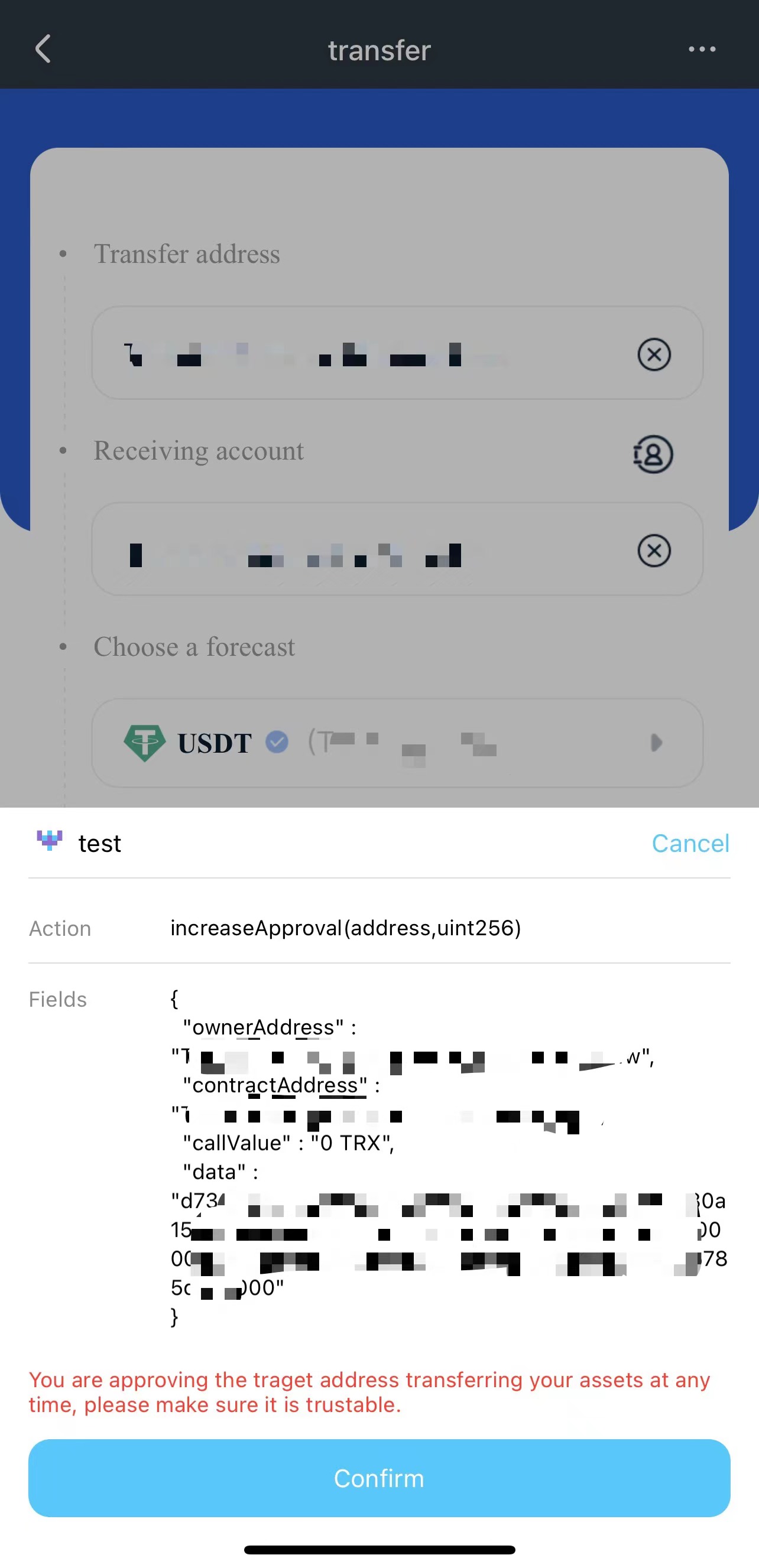
After a few days, the scammer contacted Judy again, wanting to make a large transaction. When judy transfer the tokens to his wallet address, because the wallet address was maliciously approval during the signature operation a few days ago, the tokens were immediately transferred away secretly. At this time, Judy can no longer contact the scammer.